A couple of days ago, I decided to get into bug bounty. For my non tech savvy friends, Bug bounties are programs that pay individuals - mostly ethical hackers - money for finding and reporting bugs on websites, apps, etc. An incentive against hackers selling the information on the black market instead. Being unfamiliar with the programs, I decided to pick the website at the top of the Hackerone list - BMW.
Naturally, the first thing I did was start with subdomain enumeration, there are alot of tools for this amass, sublist3r, subbrute, knock.py but my favorite is subfinder due to the speed and how easily configured it is. I always start subdomain enumeration using passive methods (The one where you just kindly ask APIs and DNS servers which subdomains they have listed rather than bruteforce guessing.). The passive enumeration misses a lot of subdomains but it takes less time and that way I can start working on the listed subdomains while the more aggressive scans take time.
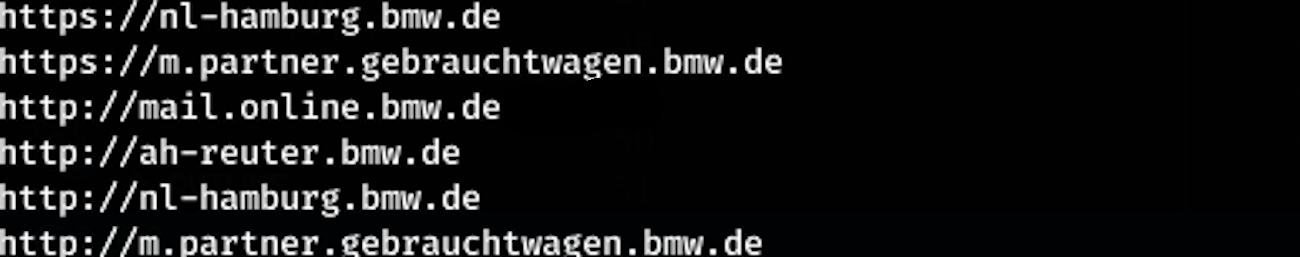
After the passive subdomain enumeration, I parsed the output to httprobe, a fast tool that checks if certain ports are open (faster than nmap btw) I set it to check for port 80 and 443, ports that traditionally host websites. While the scan went on, something caught my eye - partly because I don't speak dutch and seeing an English word I understood caught my attention and it was also because 'mail online' sounds like a treasure trove of information.
I fired up my browser and used my burpsuite app as a proxy so I could view the requests my browser was sending out. The GET request for the page returned a 302 code - Permanent redirect - back to BMW's main page. Hmmmmmmm
Rule of thumb is to probe webservers that return a redirect code (permanent and temporary redirect), developers often get sloppy believing that the redirect will keep out prying eyes.
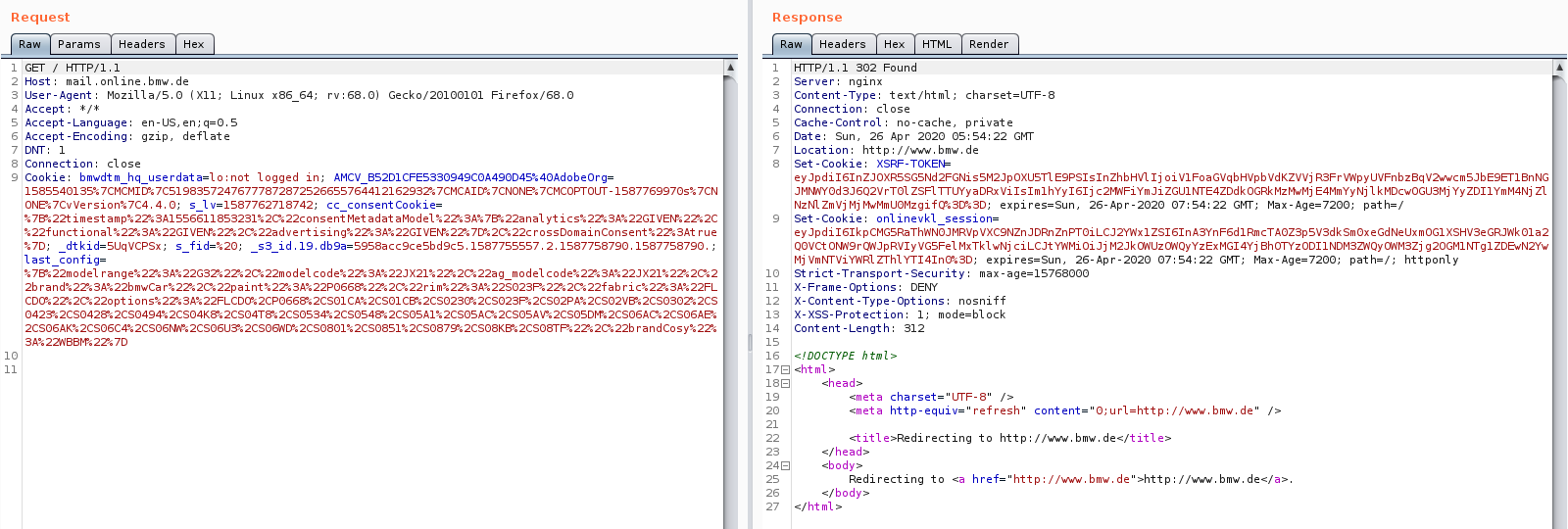
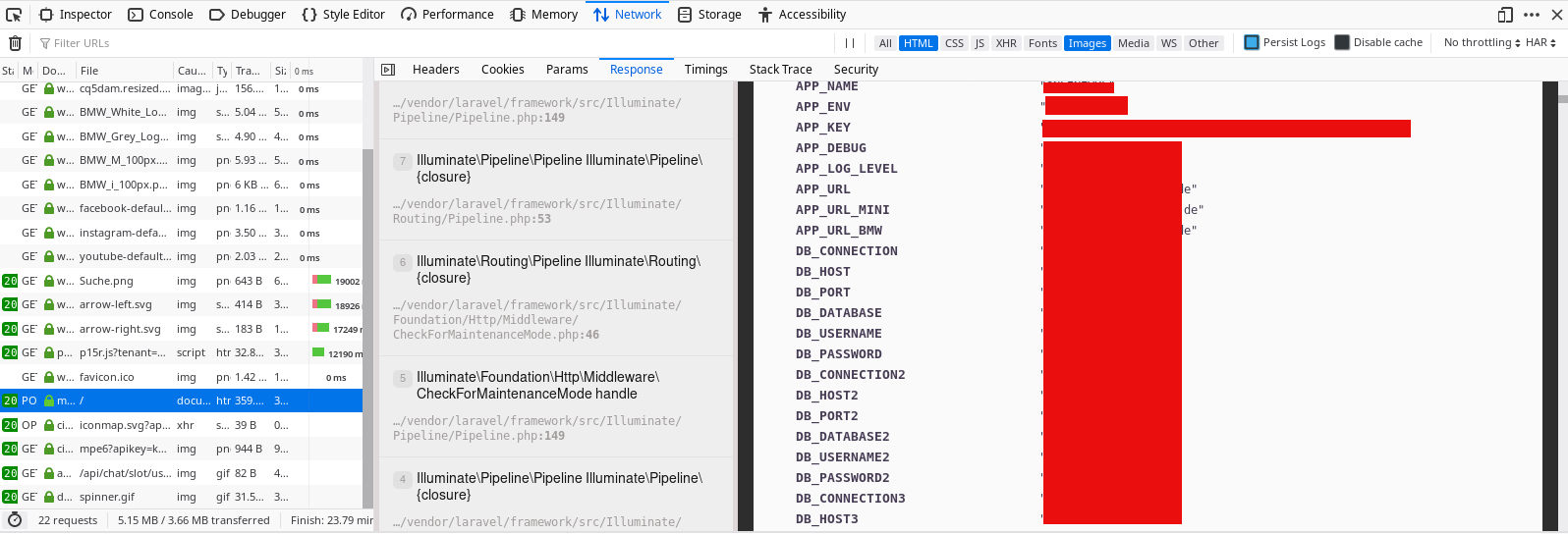
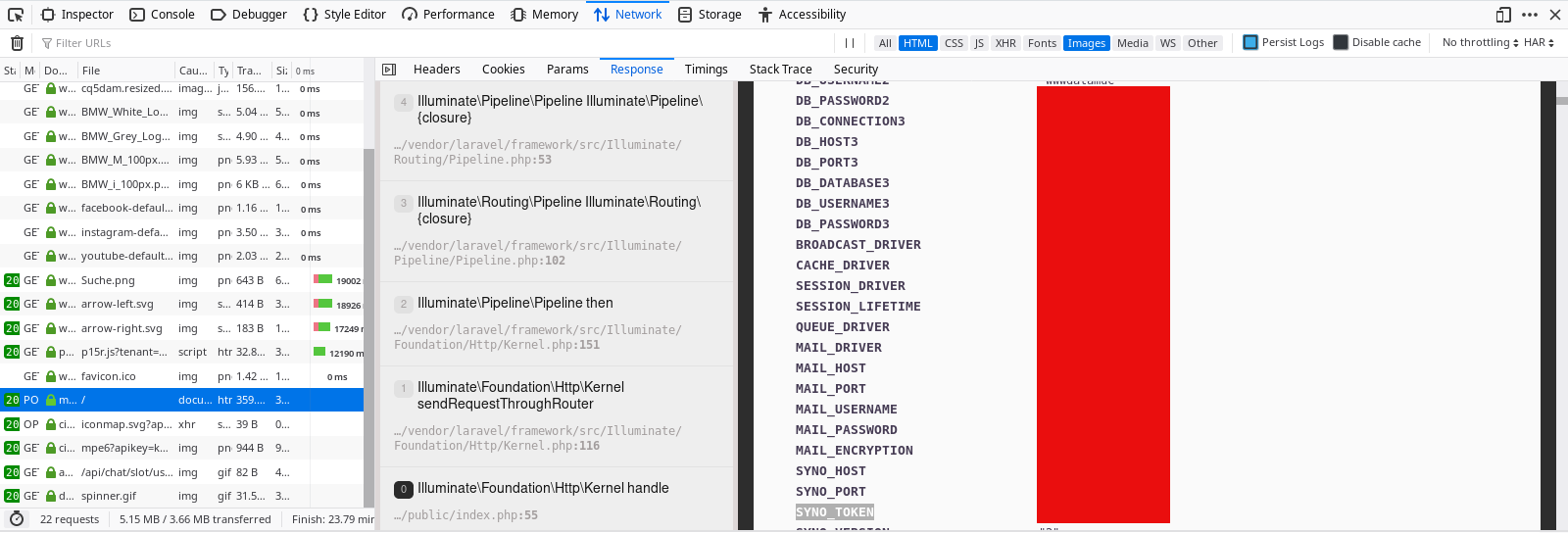
The first thing I did was switch the GET Request to a POST request just to see how the webserver handles a switch in request methods and my eyes almost popped when I saw the server response.
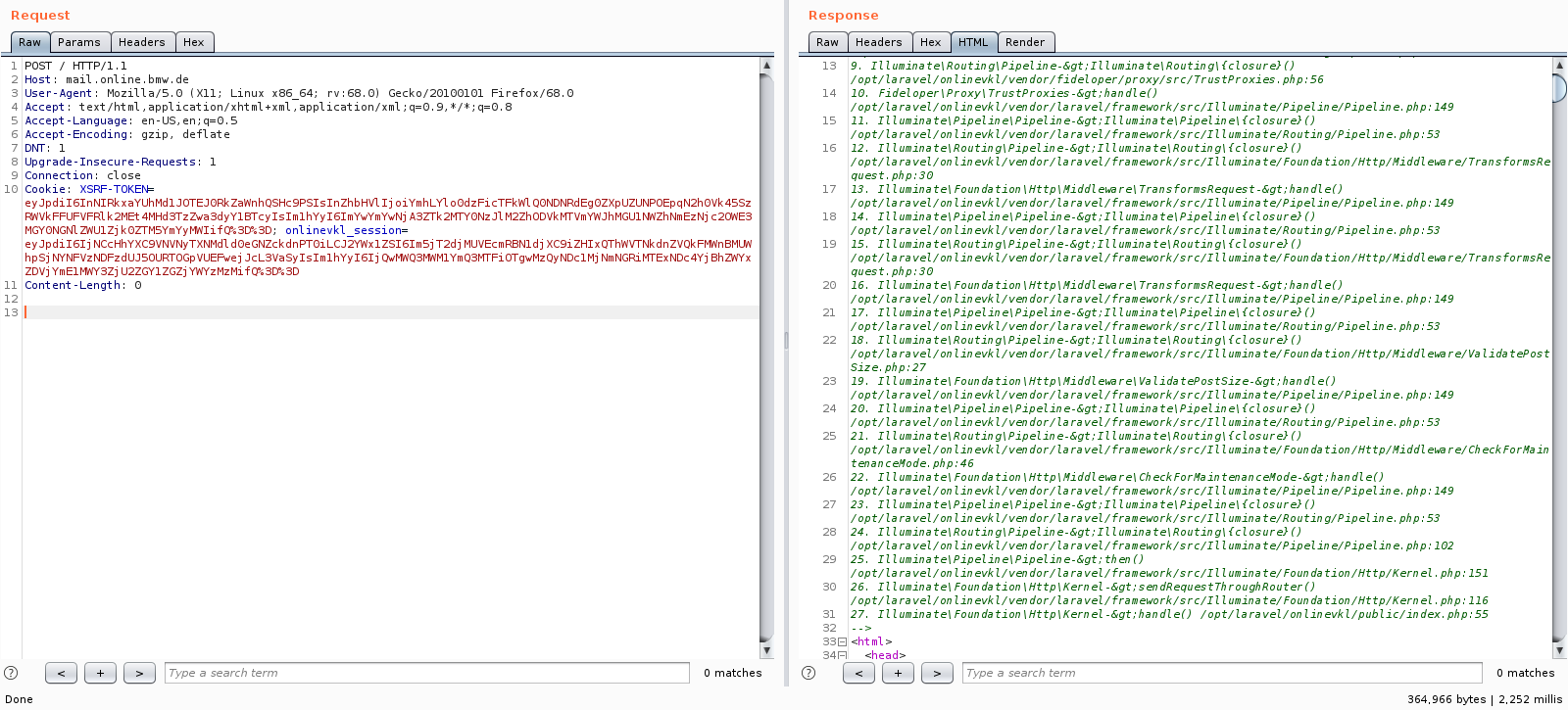
The respone was an error log message, Laravel PHP framework no doubt. I repeated the post request in my browser just to be sure (The Burpsuite render extension wasn't working because I launched Burpsuite as root). And alas it was still there but this time, my browser helped parse the page into something I could easily read and the dump included database passwords, usernames, their IPs and ports and other juicy information you dont want an hacker seeing.
Rather than use the newly gained information to push for more access, I instead decided to report it. The vulnerability was too easy to find and I knew it was only a matter of time before someone did find and report it.
HackerOne works on a first come first serve basis. And it turns out mail.online.bmw.de was out of scope... No bounty. But it was still a nice way to start my journey into bug bounties, now I know to always check what is in scope.
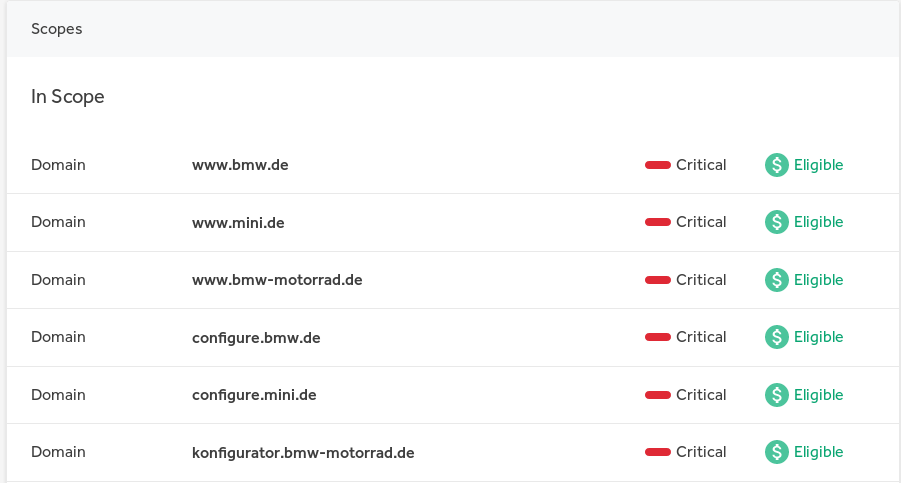
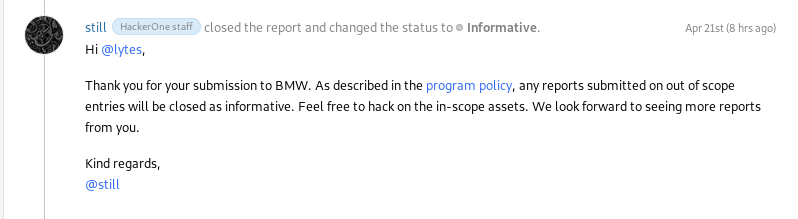
Always read the page to know what is In or Out of Scope. T_T